Audits VS Assessments And Why They Are Not The Same Thing
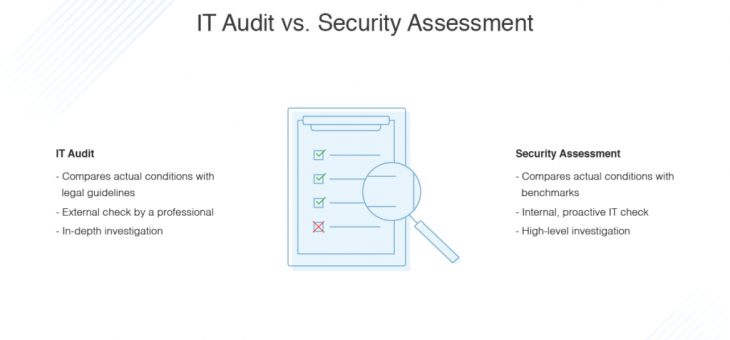
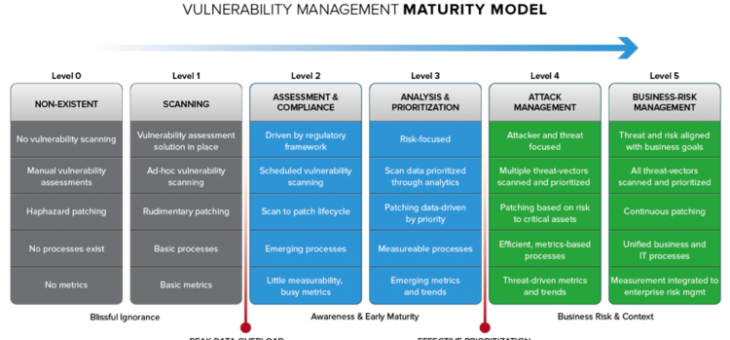
Audits vs. Assessments & why they’re not the same thing It’s much easier to mitigate a risk when you know the risk exists. Using the analogy of a snake in the grass, people don’t go running off into the woods by a creek without surveying the ground at their feet. Likewise, maintaining a blindness to risk is aRead more about Audits VS Assessments And Why They Are Not The Same Thing[…]